FIT3031 Network Security Notes
Week 1: Overview
Type of Network Attacks
- Interruption
- Availability
- Interception
- Confidentiality
- Modification
- Integrity
- Fabrication
- Authentication
Threats, Attacks, Vulnerabilities & Risks
Threats
- a malicious or negative event that takes advantage of vulnerabilities.
Attacks
- passive attack: eavesdropping, traffic analysis
- active attack: denial of service(DoS), injection
Vulnerabilities
- Flaws, e.g. lack of AUTH
Risks
- likelihood of attacks & consequence of attacks
- potential damage or loss when the threat occurs
Security Mechanisms
- Prevention
- Detection
- Recovery
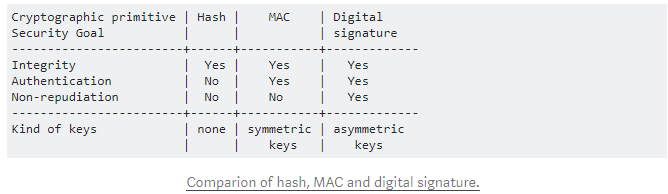
Security Goals
Secrecy/ Confidentiality(CONF)
- Encryption
Integrity
- Message Authentication Code(MAC)
- Digital Signature
Authentication
- The digital signature, biometrics, password
Non-repudiation(NR)
- The digital signature, biometrics
Availability
Crypto Overview
| Symmetric | Asymmetric | |
|---|---|---|
| Confidentiality | One-time Pad cipher, Stream ciphers, Block Ciphers | Encryption with Public Key |
| Integrity | Message Authentication Code(e.g. HMAC) | Digital Signature |
| Authentication | MAC+Nonce | Digital Signature + Nonce |
Stream cipher
- an encryption algorithm that uses a symmetric key to encrypt and decrypt a given amount of data.
One-time pad cipher:
- a randomly generated private key is used only once to encrypt a message and decrypted by the recipient using a matching one-time pad and key.
Message Authentication Code(MAC)
- The sender forwards the message along with the MAC which uses a secret key to compress the message.
- The message is sent in clear with MAC.
- The secret key is only known to the sender and the intended recipient.
- cannot achieve Non-repudiation -> we cannot identify who sent this MAC - sender or recipient?
Symmetric vs Asymmetric
Symmetric encryption
- fast
- has a key distribution problem
- Block cipher: ARS
- Stream cipher modes: RC4
Public-key encryption
- slow
- has no key distribution problem
- RSA, ElGamal
Adversarial Capability Against Encryption
Ciphertext-only adversary
- the attacker knows ciphertext by eavesdropping
Known-plaintext adversary
- the attacker knows at least one sample of both plaintext and ciphertext.
- e.g. XOR cipher can be compromised to use
plaintext XOR ciphertextto get the key
Chosen-plaintext attack
- the attacker can choose what plaintext will be encrypted.( Attacker can run the encryption functions for selected inputs)
Chosen-ciphertext Adversary
- the attacker can choose ciphertext to be decrypted.
Week 2: Public Key Infrastructure
Man-in-the-Middle (MITM) Attack
Scenario:
- Mallory intercepts
pk_aliceand forwardspk_malloryto Bob - Bob uses
pk_malloryto encrypt messages as he cannot tell the difference - Mallory intercepts Bob’s encrypted messages and decrypts them.
Solution
- Alice needs to go to a trusted party(Certificate Authority) to get a certificate.
- After verifying Alice’s identity, the trusted party issues a certificate with Alice’s name and her public key.
- Alice sends the entire certificate to Bob.
- Bob verifies the certificate using Alice’s public key - make sure it’s from Alice, not others.
- The certificate cannot be forged or tampered
Digital Signature
Use the private key to encrypt the message -> generate the digital signature
Use the public key to decrypt the digital signature -> verify the digital signature -> check if M == M'
Digital Certificate
X.509 Certificate Example
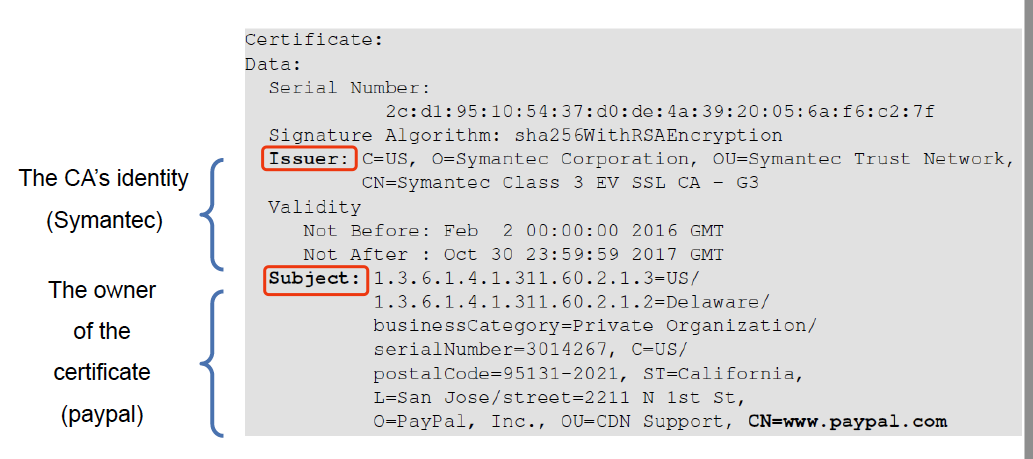
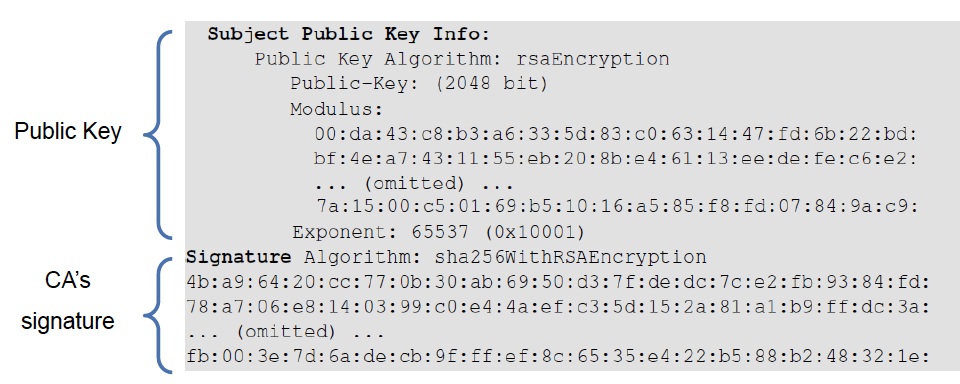
Other fields:
- Usage period
- Serial number
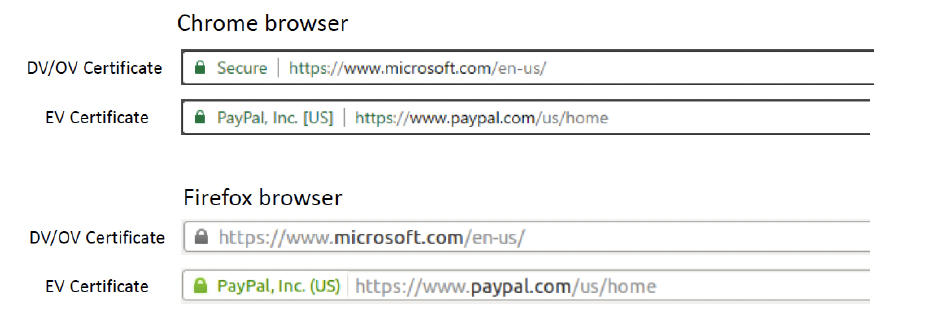
Domain Validated Certificate(DV)
The CA verifies the domain records to check if the domain belongs to the applicant(before issuing the certificate).
Domain Control Validation is performed on the domain name in the certificate request.
Organizational Validated Certificate(OV)
CAs verify the following before issuing OV certificates:
- Domain control validation.
- Applicant’s identity and address.
- Applicant’s link to the organisation.
- Organisation’s address.
- Organisation’s WHOIS record.
- Callback on the organisation’s verified telephone number
Extended Validated Certificate(EV)
CAs issuing EV certificates require documents that are legally signed from registration authorities- needs to verify the organization. (will verify the legal and proper standings of the organisation)
Digital signature in Digital Certificate
CA generates a digital signature in the certificate using its private key. Anyone can verify the digital signature to see if the certificate has been modified using CA’s public key.
Certificate Authorities
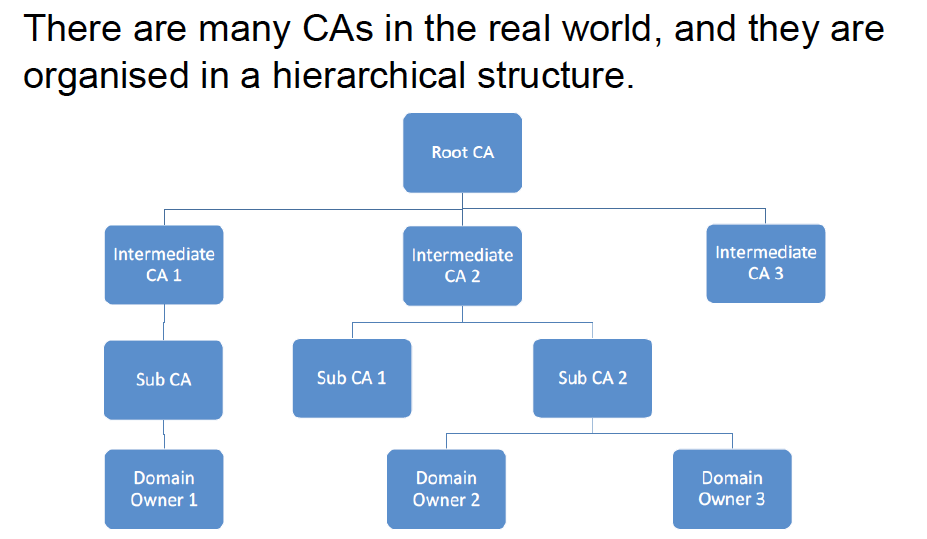
Root CA’s certificates are self-signed.
How Root CA can be trusted?
Public keys of CAs will be preinstalled in the OS, browser and other software.
Using Root CA’s public key to verify Intermediate CA’s certificate, Using Intermediate CA’s public key to verify Sub CA’s certificate.
Attack Scenario: Authentic Certificate
The attacker forwards the authentic certificate to Alice.
Alice finds the certificate is authentic so she uses the certificate’s public key to encrypt the secret and send it to the “server”.
The attacker will intercept the request but he cannot decrypt the secret because he doesn’t know the private key
Attack Scenario: Fake Certificate
The attacker creates a fake certificate for the domain example.com with his own public key.
CA will not sign the certificate as the attacker is not the owner of example.com.
The attacker tries to self-sign the certificate and sends it to Alice.
Alice’s browser will give the warning as it cannot find any trusted certificate to verify the received certificate.
Attack Scenario: Attacker’s Certificate
The attacker has his own valid certificate.
The attacker sends his certificate to Alice.
Alice’s browser checks if the certificate’s subject field matches Alice’s intent.
Attacks on PKI
The Man-in-the-Middle proxy
The proxy creates a self-signed CA certificate installed on the user’s browser.
The proxy will intercept the communication.
Attacks on CA’s verification process
Attacks on CA’s signing process: the private key is compromised
- How to protect the private key? Use Hardware Security Model
Attacks on Algorithms: Digital certificate depends on one-way hash and digital signature.
- Use stronger algorithms
Attacks on User confirmation: Some software does not compare these two pieces of information(the common name field inside the certificate and information provided or approved by user): security flaw
Week 3: Email Security
Overview Questions
- What are the principal services provided by PGP?
- Key management, Confidentiality, Integrity, Authenticity.
- What is the utility of a detached signature?
- Signatures are sent separately. Two files, original data and the signature.
- Why use R64 conversion for an e-mail application?
- Some email servers don’t accept emails in binary, it needs to be in printable characters. R64 uses ASCII character which are all printable.
- What is S/MEME? what are the cryptographic functions used in S/MIME?
- S/MIME = Encrypted MIME
- 3DES/AES for encryption, Elgamal for key exchange, SHA for signatures
- What is DKIM? How is the DKIM email authentication service different when compared to S/MIME or PGP?
- The sender’s email server signs emails
- DKIM is for email server to email server, PGP and S/MIME are end to end encryption.
Simple Mail Transfer Protocol (SMTP)
- text only
- limited to ASCII
- Size limit
- command only
- issues
- no security - clear/plain messages
Email Threats
- Authenticity
- unauthorised access
- Integrity
- unauthorised modification of emails
- Confidentiality
- unauthorised disclosure of sensitive information
- Availability
- prevent users from sending/receiving emails
TLS is not enough secure for emails, because it only secures communication between two hops. ALL intermediate hops see plaintext.
Pretty Good Privacy (PGP)
key management
AUTH + INT
- Digital signature(Non-repudiation)
CONF
- Encryption
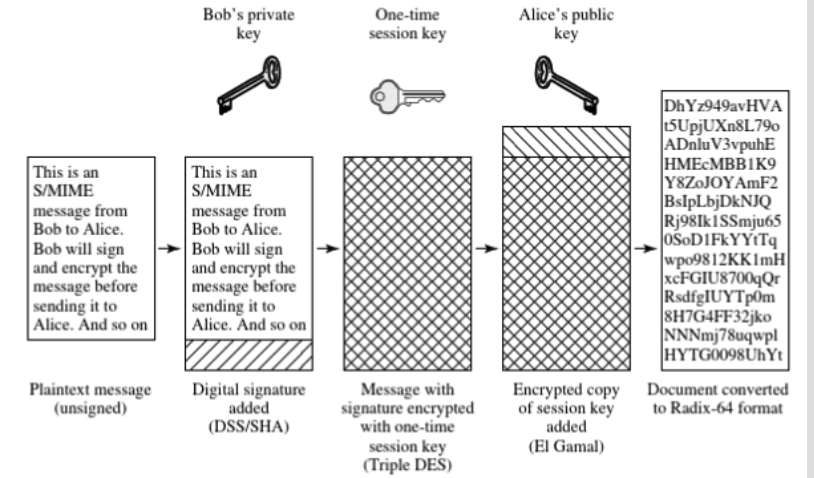
Encryption steps
- HASH(M) => digest
- RSA(digest,secretKey) => digital signature
- RSA is a public-key encryption especially used for signing.
- Digital signature || M => certificate
- Compress(certificate) => compressed certificate
- AES(sessionKey, compressed certificate) => encrypted compressed certificate(using symmetric encryption)
- RSA(sessionKey, ReceiverPublicKey) => encrypted sessionKey, used to transmit session key, another user can use his private key to get the session key.
- Send to the recipient: encrypted compressed certificate || encrypted sessionKey
Decryption steps
- Get decrypted session key using the private key => sessionKey
- Get decrypted compressed certificate using the seesionKey => compressed cetrificate
- Get M||digital signature by decompressing the data =>
M||digital signature = DeCompress(compressed certificate) - Verify hash(M) and hash(M’)
- Hash(M’) = decrypt the digital signature using the sender’s public key.
Compression
PGP uses a ZIP compression algorithm, after applying the signature and before the encryption
Why does this order matter?
- It is preferable to sign an uncompressed message so that the signature does not depend on the compression algorithm. If you do the compression first, the signatures will be different when different compression algorithms are applied.
- This has the benefit of saving space both for e-mail transmission and for file storage.
- Encryption after compression strengthens the encryption, since compression reduces redundancy in the message.
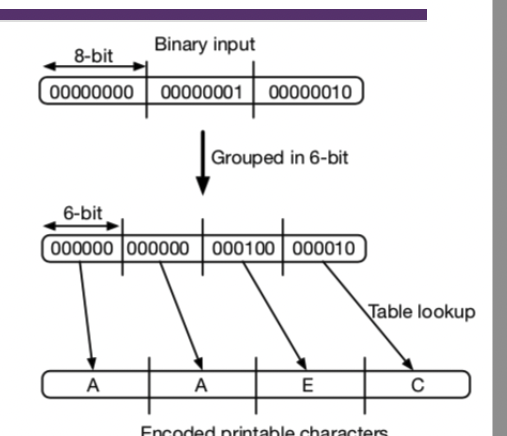
Radix-64 conversion
- used for achieving compatibility with email protocols
- text=>Binary => ASCII character, every 6bits = 1 ASCII character
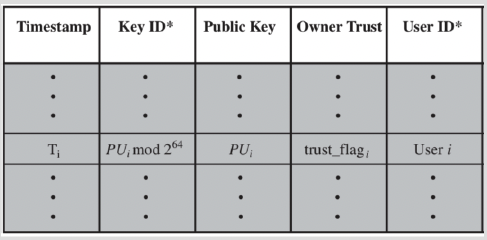
Key Management
- send key identifier(KeyID) instead of full pk for bandwidth efficiency
- users can have multiple key pairs
- two types of key rings to maintain
- her own public/private key pairs
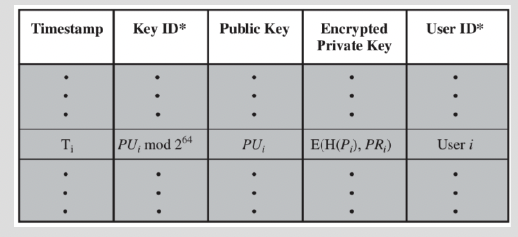
- Store encrypted private keys instead of clear private keys
- public keys of other correspondents
- all pk of other users known to the user, indexed by their key Ids.
- her own public/private key pairs
Trust Model
- not rely on certificate authorities (CAs)
- every user is its own CA
- Sign keys for users they know
- forms web of trust
- trusted keys signed
- trusted keys other have signed if there is a chain of signatures to them
Limitations
- Must exchange public key
- Target attacks against PGP keyIDs
- prevent useful functionality like search, spam filtering, topic extraction..
MIME
MIME(Secure/MultipurposeInternet Mail Extensions) supports different types of content.
Each client has a list of trusted CA’s certs and their own pairs & certs signed by trusted CA’s
Domain Keys Identified Mail(DKIM)
Tx(user)’s email must be signed by a secret key of the admin domain of Tx before leaving the domain.
Transparent to user.
Rx can verify the signature using the domain’s public key.
the public key will be stored in the DNS server, the signature will be attached to the header of the email.
Week 4: IPSec
Concepts
IPSec => network layer
IPSec secures IP datagrams at the Internet layer according to the security policy of a communicating IP node, before forwarding them to the network interface layer.
The intended receiving IP node verifies the datagrams according to the established security paramaeters and rejects any that have not been protected in accordance with the policy defined for such traffic.
IPSec Services
Authentication
- data origin authentication - verifies the claimed identify of the source data
Integrity
- connectionless integrity
- detects tampering of individual ip datagrams
- Anti-replay integrity
- detects arrival of duplicate IP datagrams
Confidentiality:
- Protects data from unauthroised disclosure and provides a limited form of traffic-flow confidentiality.
- conceals(hides) the source IP address, the destination IP address, the size of an IP datagram and frequency of communication
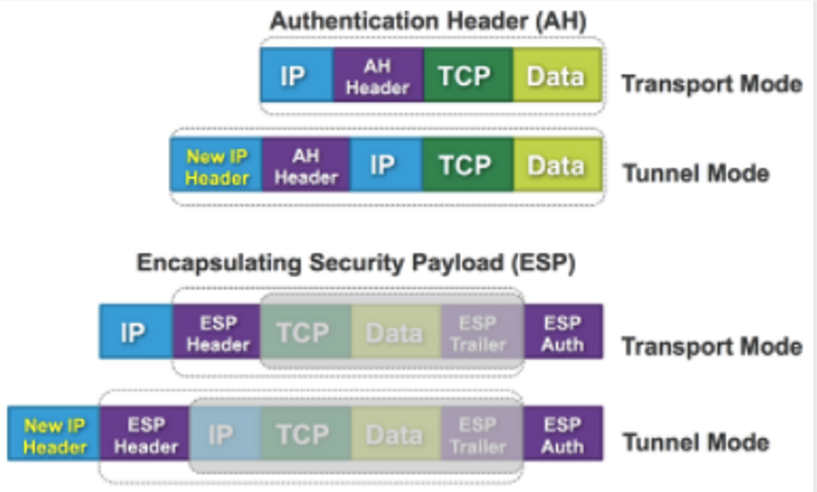
- Authentication Header(AH)
- INT, data-origin AUTH, anti-replay(Sequence number), access control, no CONF
- can only authenticate data(IP payload and selected portion of IP header), and cannot encrypt data.
- Encapsulating Security Payload(ESP)
- anti-replay, CONF
- encrypts and authenticates IP payload but not IP header
IPSec Modes
- Transport Mode
- IP packet inserted with IPsec header
- Tunnel Mode
- original packet preserved, new header added/prepended.
- ESP/AH Header is immediately after the New IP Header, original IP packet preserved
| Transport Mode | Tunnel Mode | |
|---|---|---|
| AH | Authenticates IP payload and selected portions of IP header | Authenticates entire inner IP packet (inner header plus IP payload) plus a selected portion of the outer IP header. |
| ESP | Encrypts IP payload. Allows traffic analysis | Encrypts entire inner IP packet. No routers on the way can examine the inner IP header. |
| ESP+AUTH | Encrypts IP payload. Authenticates IP payload but not IP header | Encrypts entire inner IP packet. Authenticates inner IP packet. |
Anti-replay Services
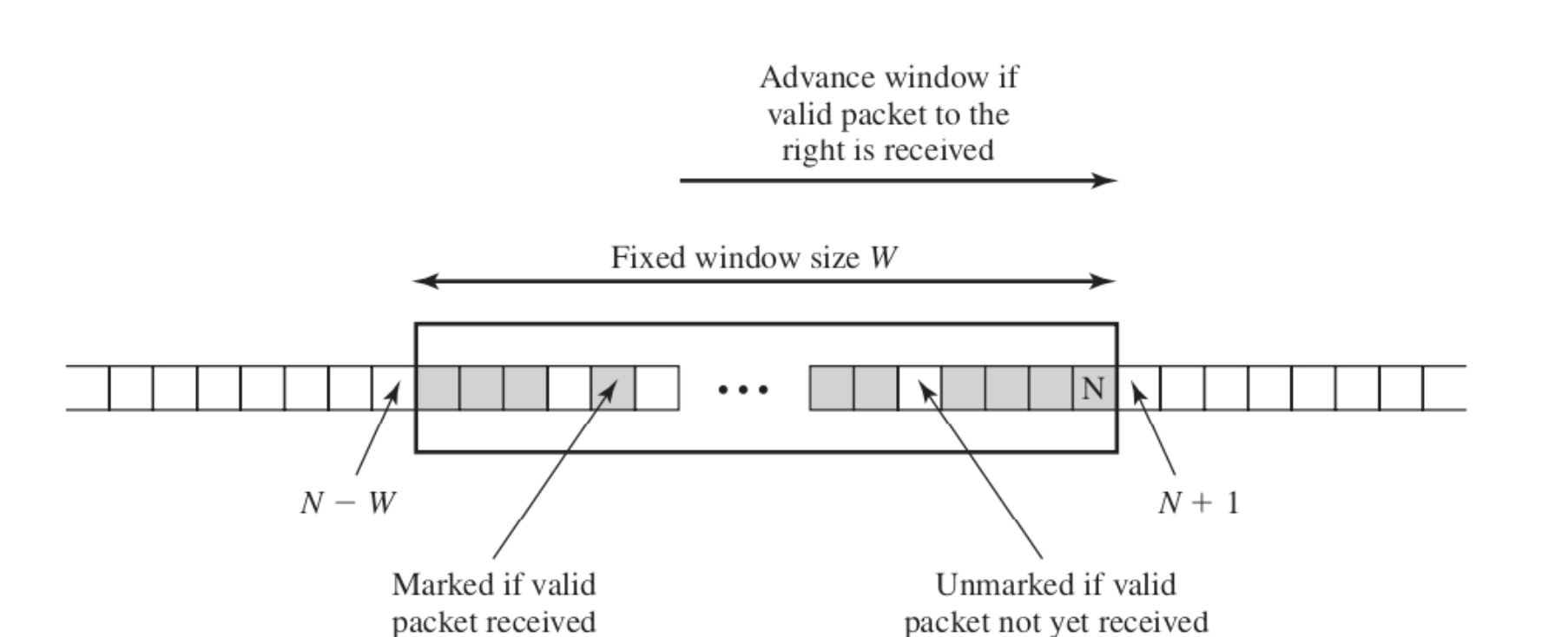
Cases
- If sequence number received now is smaller than the most left size of the current window, drop the packet.
- If sequence number received now is within the current window range, check if packet has already been recived
- If sequence number received now is greater than the max size of the current window, make the sequence number received now the max edge, and calculate the min edge through
N-W+1 - If the recipient sets N=60 and the window size W=64, range should be 0-60
Security Policy Database(SPD)
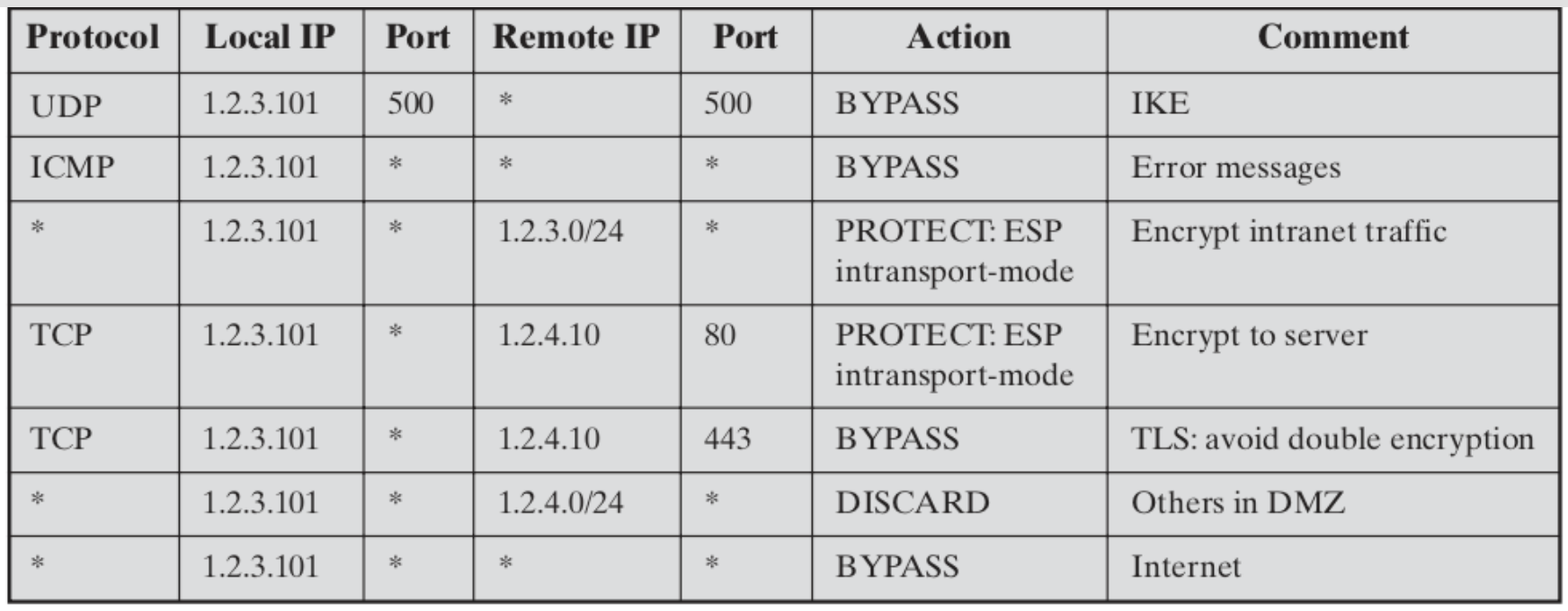
3 IPSec policies:
- DISCARD
- discard the packet
- PROTECT
- protect the packet with AH and the ESP security protocols
- BYPASS
- bypass the IPSec processing
Security Association Database(SAD)
AH info
ESP info
Lifetime of this SA
IPsec Protocol Mode
- Transparent/tunnel
IPSec Architecture
- Authentication Header(AH)
- An extension header for message authentication
- Encapsulating Security Payload(ESP)
- provides encryption for combined encryption/msg INT
- Internet Key Exchange(IKE)
- the key management schemes for use with IPSec
Virtual Private Networks(VPN)
Isolation
Tunneling
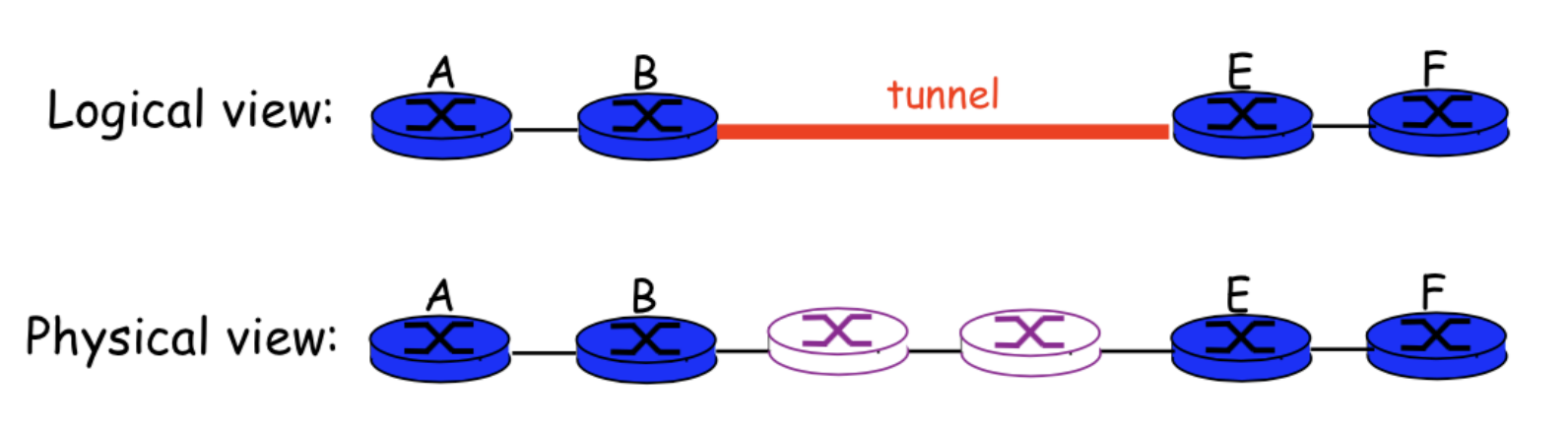
Many logical overlay networks co-exist
- over the same physical network
- provide its own dedicated service
Question
- Which one is better?
- Placing VPN server behind the firewall
- Placing VPN server in front of the firewall
- Anwser
- VPN in front of the firewall is better. VPN has the function of firewall as well, after the VPN gateway, the message will be decrypted so that Firewall can look into the details of the package.
TOR
Components for Tor
- Client
- Server
- Tor(onion) router: the special proxy relays the application adata
- Directory server: servs holding Tor router information
Process
The last router will see the clear data but not be knowing where the message from.
Every router only knows the predecessor and successor.
Send Message from client:
Client obtains a list of Tor nodes from a directory server
Client picks a random path to destination server.
Client negotiates an AES key with each router(every router has its own encryption key).
Client encrypts message
- C3 = Encrypt(K3, data||IP_Server)
- C2 = Encrypt(K2, C3 || IP_OR3)
- C1 = Encrypt(K1, C2 || IP_OR2)
Client sends an IP packet as: IP_Client || IP_OR1 || C1
- send IP packet that is consist of current router/machine’s IP, next destination’s IP and encryped message
Packet arrives at OR1 and OR1 performs:
- C2 || IP_OR2 = DEC(K1, C1)
- caches IP_Client, IP_OR2
- sents an IP packet as: IP_OR1 || IP_OR2 || C2
Packet arrives at OR2 and OR2 performs:
- C3 || IP_OR3 = DEC(K2, C2)
- caches IP_OR1 || IP_OR3
- sents an IP packet as IP_OR2 || IP_OR3 || C3
Packet arrvies at OR3 and OR3 performs:
- IP_Server || data = DEC(K3,C3)
- Caches IP_OR2, IP_Server
- sents an IP packet as IP_OR3 || IP_SERVER || data
Week 5: Transport Layer Security (TLS)
Overview
TLS sits between the Transport layer and Application layer(not belong to any of them).
- Unsurported data => given to TLS by application layer
- TLS gives protected data to transport layer.
Confidentiality
- Nobody other than the two ends of the channel can see the actual content of the data transmitted.
Integrity
- Channel can detect any changes
Authentication
- At least one end of the channel needs to be authenticated, so the other end knows who it is talking to.
Stages
Setup: TLS handshake
Secure Chanel: TLS Record
Each record contains a header and a payload.

- Break stream in series of records
- each record carries a MAC
- receiver can act on each record as it arrives
Send data process
- Get data from application layer
- Fragement
- Compress(optional)
- Add MAC and padding
- Encrypt
- Add TLS header
Receive data process
- Decrypt
- Check integrity
- use variable-length records to distinguish MAC from data

- Decompress
- Buffered
Trunction Attack
Attacker forges TCP connection close segment
one or both sides think there is less data than there actually is
Solution: record types, with one type for closure
- Type 0 for data, Type closure
POODLE Attack
it takes advantage of CBC mode (SSL V3.0).
- The client initiates handshake and sends client_hello
- The attacker intercepts via MITM attack, and impersonates the server until the client agrees to downgrade to v3.0
Attack Scenario
Attacker intercepts the channel between client and web server and injects ciphertexts
Server responses that an attacker can explore:
- Case 1: Valid ciphertext and padding
- Case 2: Invalid ciphertext with invalid padding
- Case 3: Invalid ciphertext but valid padding
Countermeasures
Remove server response
Use AES GCM model - authenticated encryption
- Ensure that the ciphertext is not modified during the transmission
Week 6: Network Attacks
Review Questions
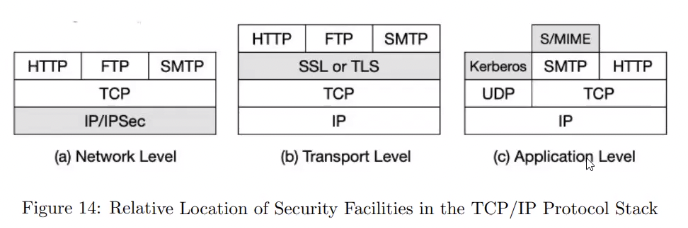
Network Level
- VPN, IPSEC
- good when you want to encrypt everything(traffic)
Transport Level
- TLS
- services provided
- Confidentiality
- Encryption
- Integrity
- MAC
- Authentication
- Confidentiality
- services provided
Application Level
SYN Flooding Attack
TCP 3-way Handshake
According to TCP 3-way handshake Protocol, when the server recievs the initial SYN pakcet, it uses TCB(Transmisson Control Block) to store the information about the connection
- This is called half-open connection as only client-server connection is comfirmed.
- The server stores the TCB in a queue that is only for the half-open connection.
After the server gets ACK packet, it will take this TCB out of queue and store in a different place.
Scenario
Continuously send a lot of SYN packets to the server using spoofed ip addresses. This consumes the space in the queue by inserting the TCB record.
Do not finish the 3rd stop of hanshake as it dequeue the TCB record
Contermeasure: SYN Cookies
- After receiving a SYN packet, the server will calculate a keyed hash in terms of the SYN packet using a secret key.
- This hash(H) is sent to the client(ip address) as the initial sequence number from the server. H is called SYN cookie.
- The server will not store the half-open connection in its queue.
- Attacker will not recived H because of the fake IP address.
- Normal client will send H+1 to the server, and server will check it.
Week Countermeasure
- Do not store any information about SYN packet.
- ACK flood attack, no corresponding ack number and seq number stored in the buffer.
TCP Reset Attack
stop the connection between two hosts.
use RST(header) packet to immediately break the conneciton.
- get corresponding information from the last packet(sequence number, source port, etc)
Can TLS mitigate this attack?
NO. TLS is on top of TCP, TLS cannot protect the header of TCP, so RST can still be set.
Solution:
- IDS
TCP Session Hijacking Attack
What can a hacker do?
Capture the packet and get the
next sequence numberandacknowledgement numberForge a packet using the information got previously.
- Trying to make the packet valid
Successfully take over the session
Solution
- making it difficult for attackers to spoof packets
- Randomise initial sequence number
- Randomise source port number
- Encrypting TCP payload and header
- making it difficult for attackers to spoof packets
DNS Protocols
Authoritative Name Servers
- Each DNS zone has at least one authoritative nameserver that publishes information about the zone.
- It provides the original and definitive answers to DNS queries.
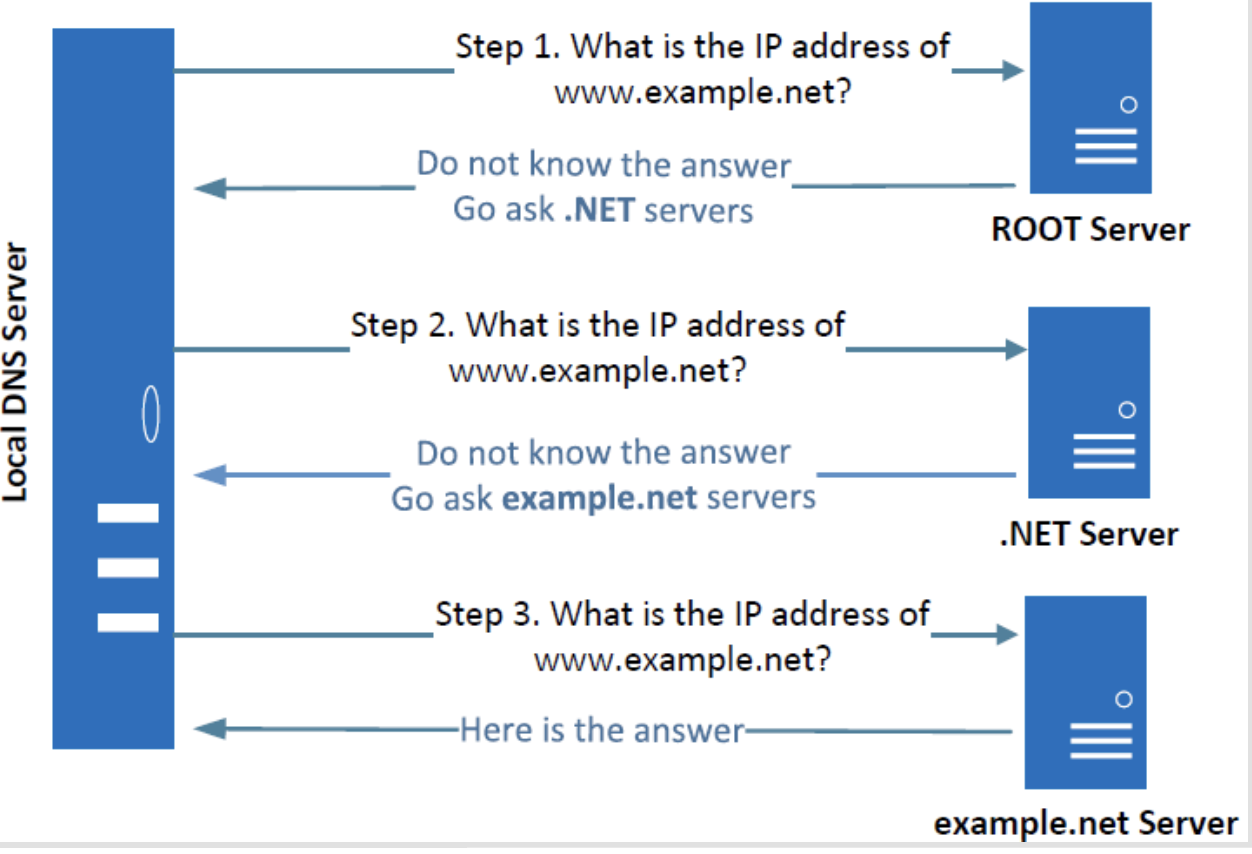
Local DNS cache poisoning attack
- Attack on user machines
- attacker sends a fake DNS response with an evil IP address to the user machine which sent out a DNS query.
- Attack on local DNS server(Cache Poisoning attack)
- When the local DNS server sends out iterative queries to get an answer from the DNS servers on the internet, attackers can send out spoofed replies to the local DNS server.
- They get accepted as long as they arrive before the actual replies.
Remote DNS cache poisoning attack
Remote DNS cache poisoning attack needs to guess the port number, transaction ID, etc.
Cache effect: if no attempt fails, the actual reply will be cached by the local DNS server; the attacker needs to wait for the cache to timeout for the next attempt.
The Kaminsky Attack: ask a different question every time, and guess the transaction id and port number.
Countermeasures
DNSSEC
- provide authentication and integrity checking on DNS data, not confidentiality.
- No client/server setup “dialog”.
- Check digital signatures -> check if the information is authentic or not.
- depend on trust in the Root Name Server’s key, and all other signing keys
TLS/SSL
- Client & server agree on crypto, session keys
- depend on trust in Certificate Authorities/decision to sign keys
Week 7: Wireless Security
Overview
Basic building block of an 802.11 WLAN:
- AP(BSS) and clients
Define an Extended Service set
- Network of multiple BSS using Distribution System. e.g. eduroam
Security areas addressed by IEEE 802.11i
- Authentication, Confidentiality and integrity.
Difference between TKIP and CCMP
TKIP(Temporal Key Integrity Protocol) was introduced to improve security of WEP
CCMP(Computer mode anad Cipher Block Chaining Protocol) is sued in WPA2, it provides authentication, integrity and confidentiality.
Threats
- Man-in-the-Middle attack
- Identity theft, media accesss control(MAC) address spoofing
- Ad hoc networks
- Denial of Service(DoS)
- Network injection
Wired Equivalent Privacy(WEP)
Improper IV management
- Can detect when IV reused
- IV collision
- Can detect when IV reused
WEP recommends
- IV changed per packet
- some WEP implementations weak
Messages can be modified without knowing the key
CRC32 not a MAC
- is linear
CRC32 used with a stream cipher
- stream cipher is linear
can modify ciphertext without disctributing m
WPA2
The 4-way handshake
- used to connect to any protected Wi-Fi network
- provides mutual authentication
- Negotiates fresh PTK: pairwise temporal key
Reinstallation Attack
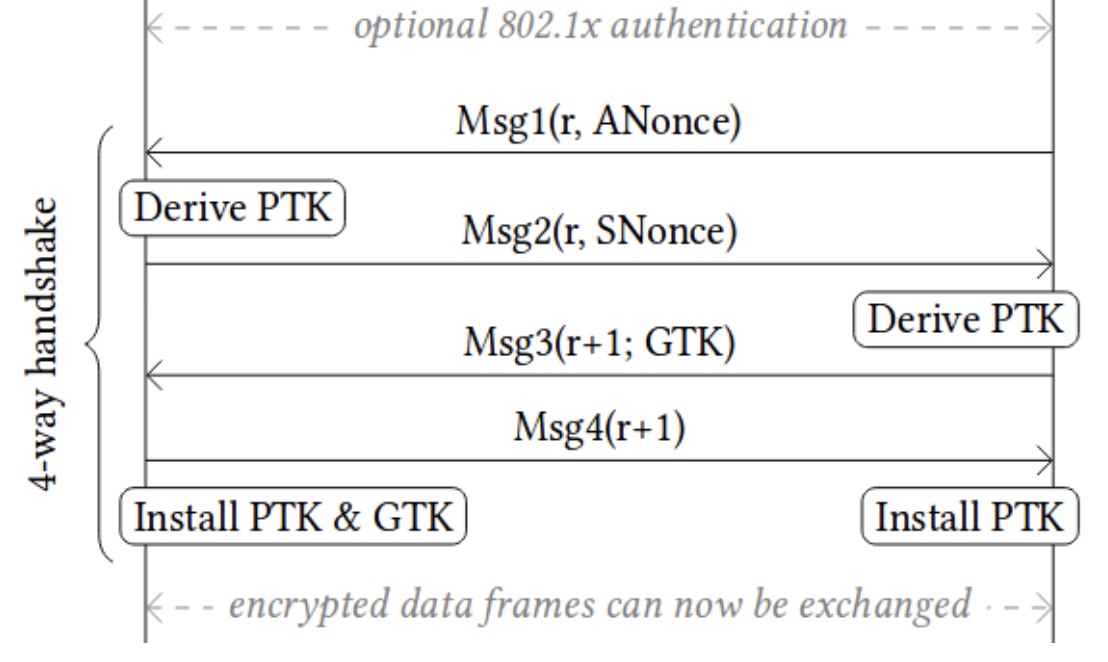
After the client receives msg3, the client will install the key. Once the key is installed, it will be used to encrypt data frames and send msg4 to AP. If AP did not receive msg4, it will re-transmit the msg3, client will re-install the same encryption key and thereby reset the incremental transmit packet number (nonce) and receive the replay counter used by the encryption protocol.
As a result, the same encryption key is used with nonce values that have already been used in the past. In turn, this causes all encryption protocols of WPA2 to reuse keystream when encrypting packets. In case a message that reuses keystream has known content, it becomes trivial to derive the used keystream. This keystream can then be used to decrypt messages with the same nonce.
Solution
- Do not retransmit message 3/4
Jamming
Transmitting a continuous jamming signal or several short jamming pulses causes DoS
Detection
monitor signal strength
monitor carrier sensing time
Week 8: Intrusion Detection System(IDS)
Intruders
Masquerade
- outsider in general
Misfeasor
- Insider in general
Clandestine
- can be both
Design Goals
- Detect a wide variety of intrusions
- cover known and unknown attacks
- Adapt to new attacks or changes in behaviour
- Detect intrusions in real-time
- analyse user activities efficiently
- Report suspicious cases timely
- Ensure accuracy
- minimise false positives and false negatives
IDS Models
- Signature-based
- unusual behaviours are known
- pro
- effective and efficient at detecting known threats
- less false positive
- Raise alarm when activities match the signature
- con
- ineffective at detecting unknown threats and many variants of known threats
- cannot track and understand the state of complex communication, so it cannot detect most attacks that consist of multiple events.
- hard to keep signature updates
- Anomaly-based
- Usual behaviours are known
- Raise alarm when activities deviate from the usual behaviour
- pro
- can detect the unknown attack
- can use a new user profile to update
- con
- it requires more time and processing capacity than signature-based IDS(less efficient to identify the behaviours)
- it may generate false positives(a normal activity is recognised as malicious) and false negative(a malicious activity is recognised as normal)
- Heuristic-based
- Use a machine learning model for normal behaviour
- Raise alarm when activities are identified as abnormal by the model
- pro
- reveal the hidden pattern in complicated data
- it is adaptive to the change in users’ behaviours
- con
- Lack of training data
- a model can be poisoned by adversarial input
- still have many false positives
IDS Architecture
Auditor
- record all security-relevant activities for analysis
Analyser
- Automatically analyse the data from the auditor
- update auditor and analyser settings when needed
Notifier
- Report detected anomaly
- Update auditor and analyser settings when needed
- Initiate countermeasures
IDS Types
- Host-based IDS
- Deploy in local system to detect malicious activities on a single device.
- It can be sued tas a distributed system in the network.
- Pros
- low cost since most of the HIDS is software-based
- can see low-level activities
- low error rate for local threats
- Cons:
- limited view on the network
- malicious insider can tamper the system
- Network-based IDS(NIDS)
- Monitor the traffic on the entire network to detect instrusions
- Pros:
- can see attacks in network traffic especially in Transport layer or IP layer.
- Hard to temper
- Cons
- dedicated hardware may be needed.
- difficult to check the encrypted traffic.
Firewall
Overview
A network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules.
Cloud-based Web Application Firewall
- In-house hardware firewall => virtualisation
- Reduced local cost increased service scalability
- Concern on Privacy
- Traffic contains sensitive information
- Rules are also proprietary
- Threats
- Cloud(insider) or attacker that breaks into the cloud are interested in rules and traffic contents
- Concern on Integrity
- Cheating service provider
- Software bugs misconfigurations
Sliding-window Based Tokenisation
Att->tta->tac->ack->cke->ker- like a sliding window
- divides the words into small windows and make rules to detect malicious words.
Issues
Will consume a lot of memory, may slow down your network.
It may drop some of non-malicious or the original legitimate traffic because you made the rules and that pattern may actually occur in other strings.
The large brandwith cost.
Frequency analysis happens will there are the same contents since the same strings will be encrypted to the same token.
Solution
Cloud firewall should only know matches on suspicious strings
Adding salt

- Trade-off
- The needed storage of the rules increased
- The storage of the gateway needs to be increased(for storing counters)
Limitations of current protocols
The large brandwith cost due to sliding-window-based tokenisation
Limited functionality - only pattern/header matching only
Stateful & Stateless Firewall
Stateless filrewall takes every packet independently to decide whether to drop it or not, because it does not save the state.
- consume a lot of resources
Stateful Firewall
Get a few packets add see if they are allowed to acually go through.
Stateful firewalls intercept packets at the network layer and then derive and analyze data from all communication layers to improve security. Information about connection state and other contextual data is stored and dynamically updated.
Challenges
- need more spaces to store the states.
Week 10: BGP and BGP Security
Autonomous System (AS)
Autonomous System in networking is a collection of one or more associated Internet Protocol (IP) prefixes with a clearly defined routing policy that governs how the AS exchanges routing information with other autonomous systems.
ASN
- Autonomous System Number(ASN) is a globally unique identifier of a AS
AS Path
- AS Path Attribute is a list of AS numbers that the router traverse to reach a destination IP/Network.
BGP Speaker
- A router running BGP is a BGP speaker
BGP Peer
- Two routers that have stablished connections for exchanging BGP information
Types
- Stub AS
- end customers, do not provide transit to others
- Transit AS
- Provide transit to others
- Stub AS
Types of BGP connections
- EBGP(External BGP)
- For BGPs from different AS
- IBGP(Internal BGP)
- For BGPs from the same AS
Border Gateway Protocol (BGP)
IP Prefix Announcement
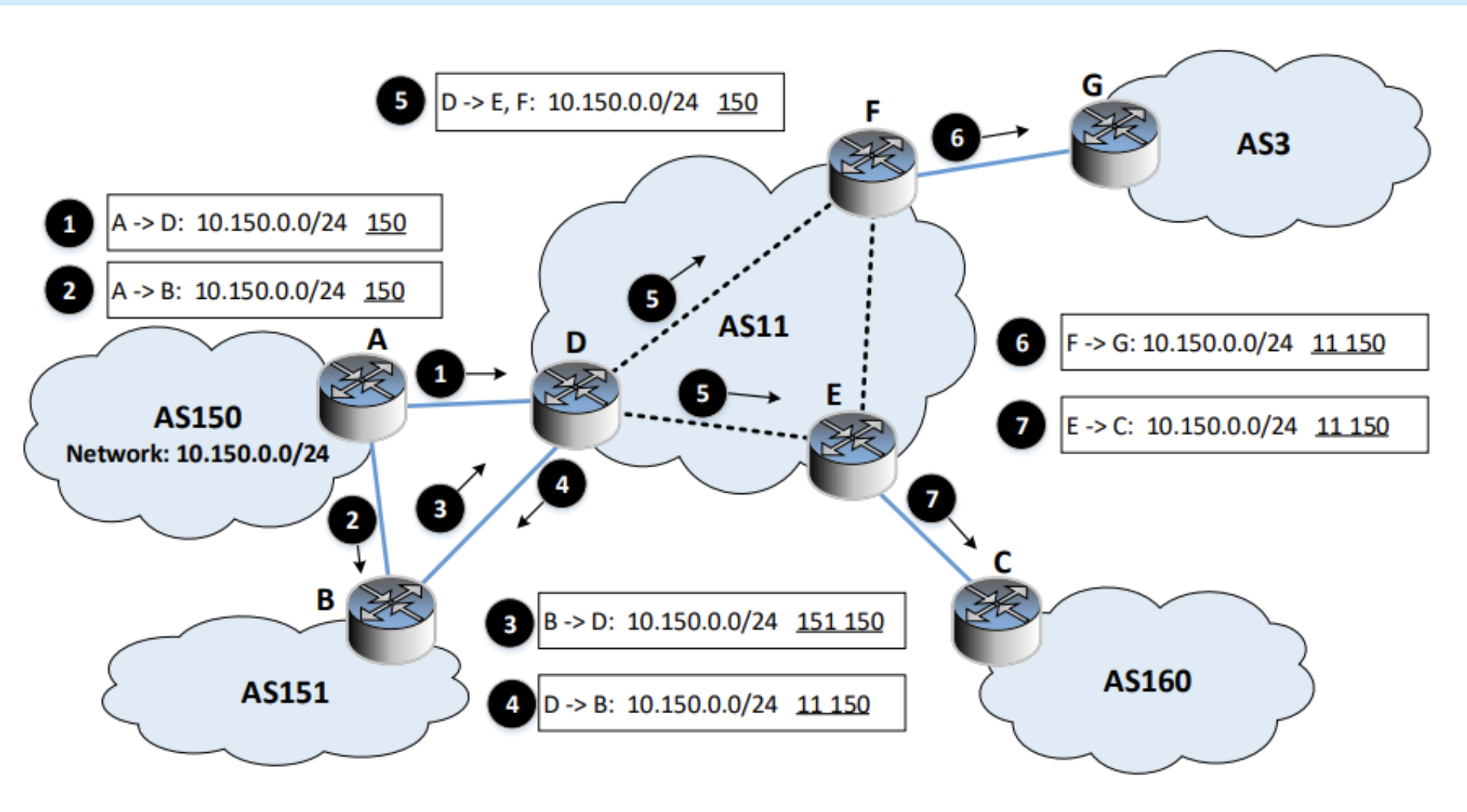
Path selection: by default, the selector will choose the shortest path.
IP Anycast
- Multiple machines share the same IP
- Naturally supported by BGP
- Routing decides which one gets the packet
Routing Rule
- Longest match wins
- e.g. packets to 10.164.0.71 will match both 10.164.0.0/25 and 10.164.0.0/24
- 10.164.0.0/25 will be selected because it has 25 bits of the match, while the second only has 24bit of the match.
- BGP Hijacking Attack
- BGP does not have a mechanism to verify the ownership of a network perfix
- Malicious BGP routers can announce fake network prefixes
- Solution
- Filtering: Active monitoring
- Using filters, we can block the prefixes with longer lengths
- Resource public key infrastructure
- new route needs to be signed by a trusted authority
- Verify the ownership of IP prefix
- BGPSec
- it is cryptographically and authenticating the whole path in BGP messages. When it reaches one of. the router, it will have signatures from everyone so that you can verify that where it comes from.
- Filtering: Active monitoring
- e.g. packets to 10.164.0.71 will match both 10.164.0.0/25 and 10.164.0.0/24
Week 11: Denial of Service Attack
Goals
Target on availability
- take out a large site with little computing work
How: amplification
- a small number of packets => big effect
DoS bug -> design flaw
DoS flood -> command bot-net to generate a flood of requests
Mitigation
- Client puzzles
- given challenges
- for TCP connection floods, the first data must contain a puzzle solution, otherwise, the TCP connection is closed.
- for SSL hanshake DoS
- Challenge C based on TLS session ID
- Server: check puzzle solution before RSA decryption
- Limitations
- Requires changes to both clients and servers
- Hurts low-power legitimate clients during an attack
- CAPTCHAs
- Source identification
- identify packet source
- block the attack at the source
- Ingress filtering
- ISP only forwards packets with legitimate source IP
- Traceback
- DDoS involves many packets on same path
- Store one link in each packet
Countermeasures
Prevent initial hack
Use of firewalls
Check ingress/egress packets
Use a server farm and load balancer to offset the effects of a DDoS attack
Change the IP address of the attacked system
