SSL/TLS Protocol
Introduction
SSL stands for Secure Sockets Layer, and TLS stands for Transport Layer Security. TLS is an updated and more secure version of SSL. Nowadays, the SSL has been deprecated and replaced with TLS, therefore, we will use the term “TLS” to explain this protocol.
SSL/TLS protocol is used to achieve the following goals
- CONFidentiality
- INTegrity
- AUTHentication
A very common use is HTTPS. HTTPS is the HTTP protocol with data encryption using SSL/TLS.
TLS Handshake Explanation
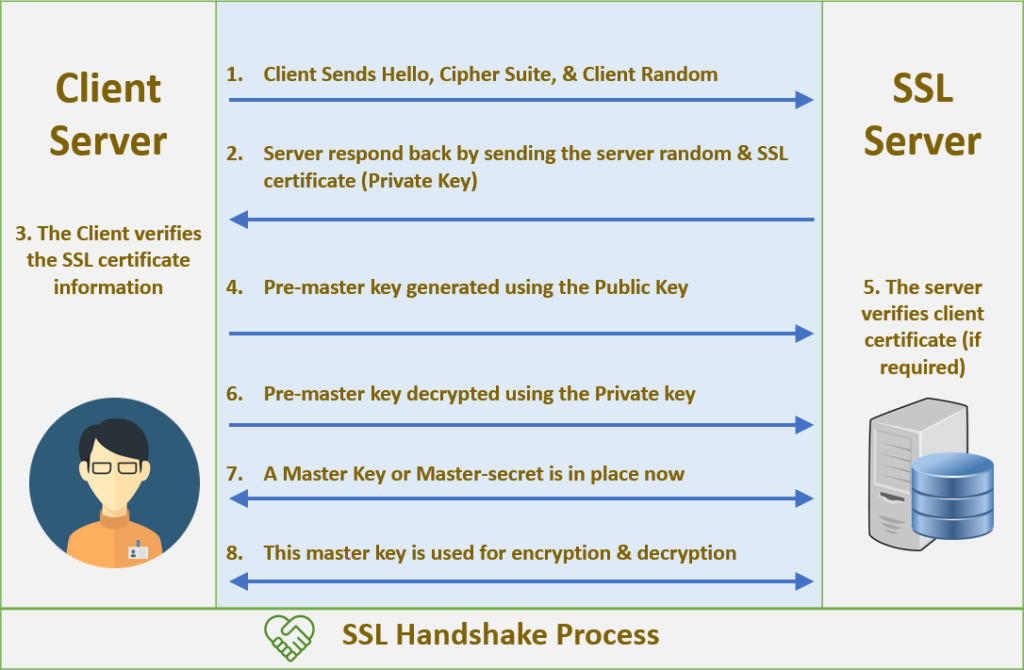
Client sends hello, supported TLS version, supported cipher suite and Random(client random string).
Server sends message “server hello” back to the client, and also responds with chosen cipher suite, server random string, and SSL certificate(with server’s public key).
The client will verify the SSL certificate information, get the public key of the server.
Client sends pre-master key generated using the public key he just got from the server.
Server decrypts the pre-master key from the client by using his private key.
Both client and server use “client random”, “server random” and pre-master key to generate the same shared key using the same algorithm
Client is ready: client sends “finished” message which is encrypted by the shared key.
Server is ready: server sends “finished” message which is encrypted by the shared key.
Handshake is finished, server and client use symmetric crypto to communicate with each other.
How SSL/TLS protocol prevent attack
Scenario 1
Attacker intercpet the message sending from the client to the server, direct it to themselves, and the attacker itself will send hello message to the client. Server will send its certificate to attacker and attacker will send this back to the client.
Solution
Eventhough the client verified the certificate, the attcker has no idea what the private key of the server, so he cannot decrypt the key transport and also cannot get the shared key generated later.
Scenario 2
Attacker sends client a fake certificate for google.com, will client uses the fake public key to generate a symmetric key?
Solution
After receiving the fake certificate, client would look up from the online public database for the public key of the certificate received to verify the certificate. Obviously, the certificate is fake and the website will then be labelled as not secure and the attack failed.
Common Attacks
SSL Stripping Attack
Attacker modifies web traffic to trick a client into accepting http connection instead of https
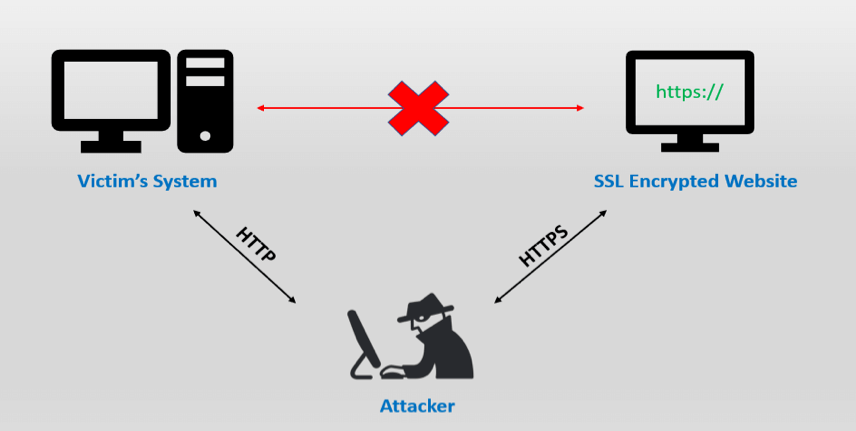
Countermeasure
Server tells browser upon first visit to only accept HTTPS(not HTTP) for future requests to this domain.
BEASAT/POODLE
Browser Exploit Against SSL/TLS / Padding Oracle On Downgraded Legacy
- Attacker exploits Bugs in encryption/MAC mode of operation algorithm in TLS 1.0 to extract information on secret key.
Countermeasure
Patches to TLS algorithms/implementations.
Compression ratio info-leak Made Easy(CRIME)
TLS has a compress-then-encrypt mode; Compressed data length no hidden by encryption, reveals information to attacker on secret web site cookies.
Countermeasure
Disable TLS compression, avoid if possible record layer compression.
IPsec Protocol
Introduction
IPsec stands for Internet Protocol Security, and is common used by VPN(Virtual Private Network).
IPsec methods
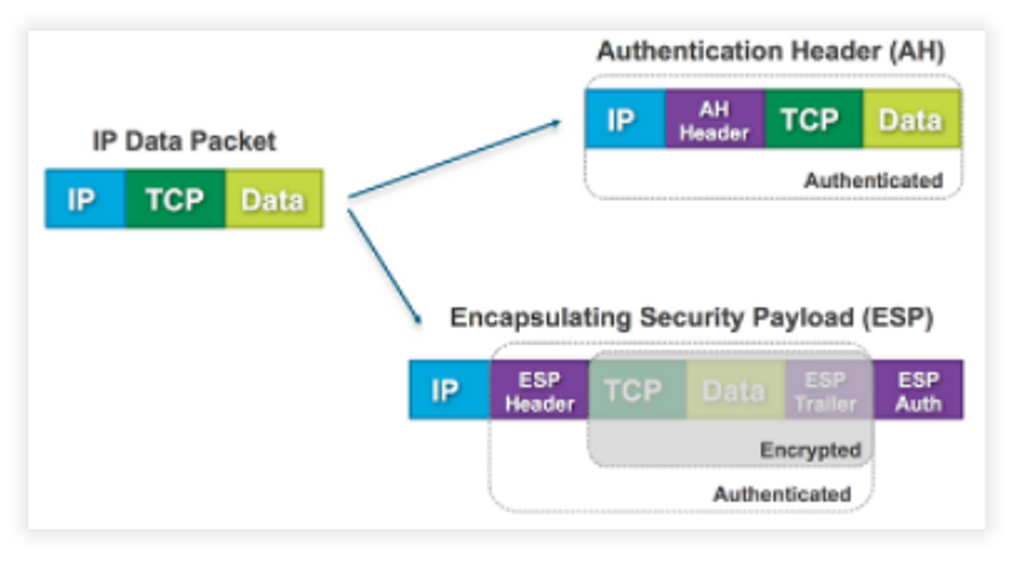
AH - Authentication Header
AH can only authenticate data, and it cannot encrypt data. It adds an Authentication after the original IP header. AH authenticate the whole IP packet.
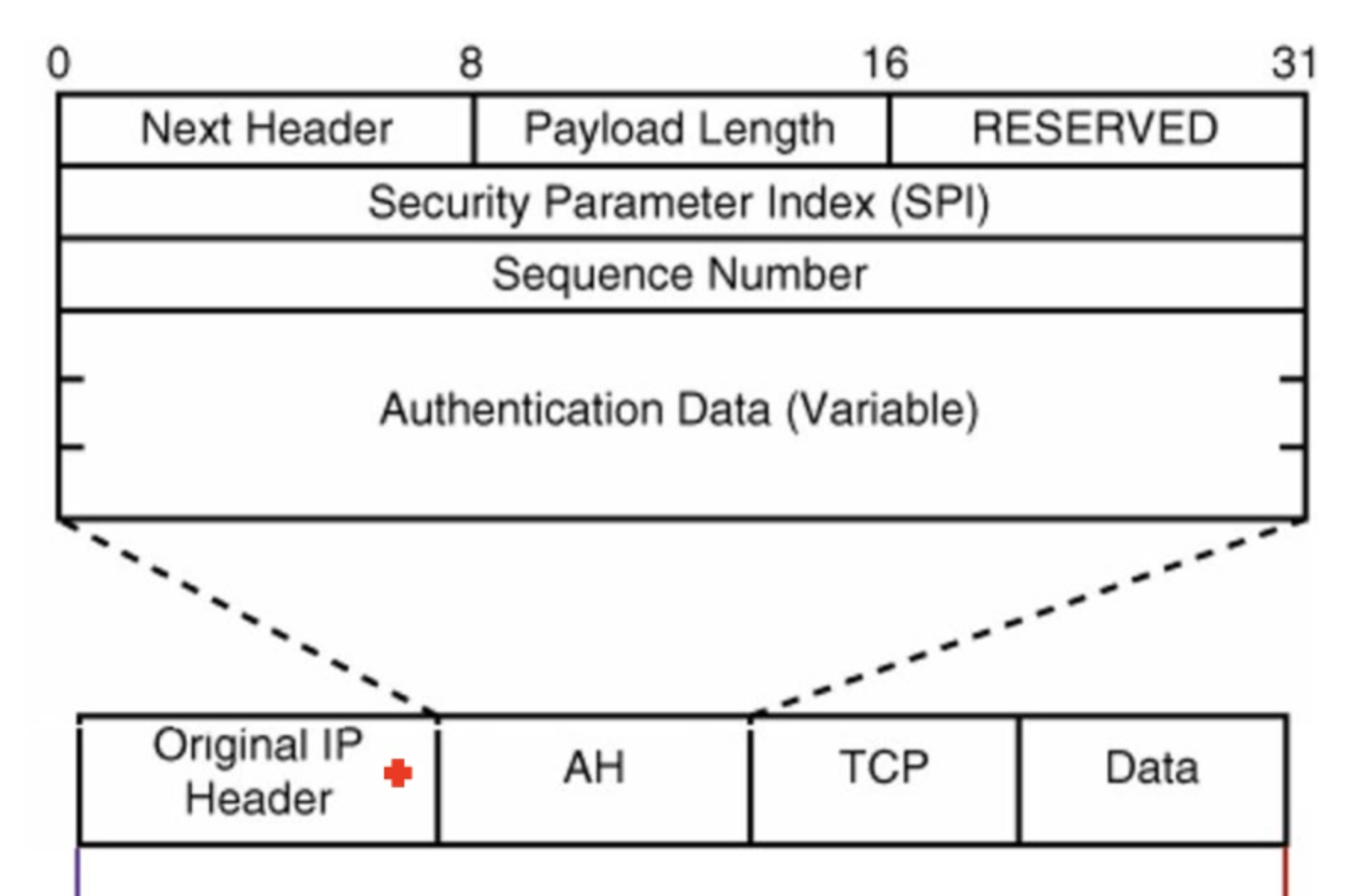
Security parameters index: point to entry corresponding to browser/server; includes info on shared key.
Sequence Number is used for freshness vs replay attacks
ESP - Encapsulating Security Payload
ESP supports both Authentication and Encryption. However, ESP does not encrypt and authenticate the IP header.
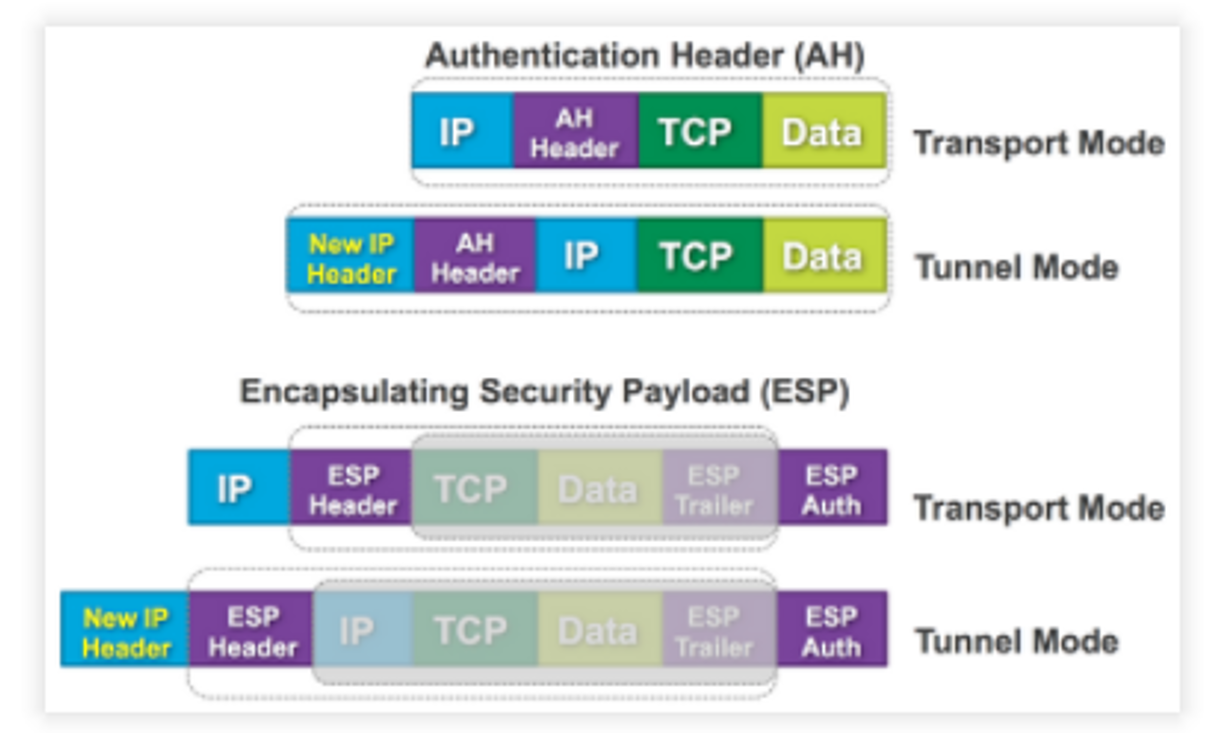
Modes
- Transport Mode
- IP packet inserted with IPsec header(AH header/ESP header)
- Tunnel Mode
- original packet preserved incl original header, new header added/prepended(at the begining of the whole packet)
PAN
Introduction
PAN stands for Personal Area Network. This technique is mainly used by Bluetooth.
Bluetooth’s Secure Connections
leverage on human channel during pairing, e.g.
compare passkey on both devices
see passkey on one, type into the other
type same passkey into both
which option, depends on device I/O capability
Reference
Monash Uni FIT2093